Nagios NRPE
Downloading Nagios Core:
https://www.nagios.org/downloads/nagios-core/thanks/?t=1500128149
Installing Nagios Core:
Installation is really easy just follow the guide:
Once it's installed, create a host and a service and the commands.
Lets start by making sure nagios sees the files we are going to create for our hosts and services.
vi /usr/local/nagios/etc/nagios.cfg
cfg_file=/usr/local/nagios/etc/hosts.cfg
cfg_file=/usr/local/nagios/etc/services.cfg
We will start by creating a template we can use for our hosts, then below we will create the host and then create the services for that host.
vim /usr/local/nagios/etc/servers/hosts.cfg
define host{
name linux-box ; Name of this template
use generic-host ; Inherit default values
check_period 24x7
check_interval 5
retry_interval 1
max_check_attempts 10
check_command check-host-alive
notification_period 24x7
notification_interval 30
notification_options d,r
contact_groups admins
register 0 ; DONT REGISTER THIS - ITS A TEMPLATE
}
define host{
use linux-box ; Inherit default values from a template
host_name linux-server-01 ; The name we're giving to this server
alias Linux Server 01 ; A longer name for the server
address 192.168.1.100 ; IP address of Remote Linux host
}
vim /usr/local/nagios/etc/servers/services.cfg
define service{
use generic-service
host_name linux-server-01
service_description CPU Load
check_command check_nrpe!check_load
}
vi /usr/local/nagios/etc/objects/commands.cfg
The -H will be for the host it will connect to (192.168.1.100) defined in the host.cfg, the -c will be the name specified on the remote host inside the /etc/nrpe.cfg
define command{
command_name check_nrpe
command_line $USER1$/check_nrpe -H $HOSTADDRESS$ -c $ARG1$
}
Verify nagios config for errors before restarting.
/usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfg
Restart the service
service nagios restart
Remote host:
now lets install the NRPE plugins and add a few plugins to the config file.
To view the list of plugins you can install:
yum --enablerepo=epel -y list nagios-plugins*
yum install nrpe nagios-plugins-dns nagios-plugins-load nagios-plugins-swap nagios-plugins-disk nagios-plugins-procs
Now we need to add the nagios server (192.168.1.101) and the commands it can execute
vim /etc/nagios/nrpe.cfg
command[check_dns]=/usr/local/nagios/libexec/check_load -w 15,10,5 -c 30,25,20
allowed_hosts=127.0.0.1,192.168.1.101
systemctl enable nrpe
systemctl restart nrpe
Now go back to the nagios server and check if it connects.
check_nrpe -H 192.168.1.100
Other NRPE commands:
command[check_ping]=/usr/local/nagios/libexec/check_ping 8.8.8.8 -w 50,50% -c 100,90%
command[check_diskusage]=/usr/local/nagios/libexec/check_disk -w 20% -c 10% -p /dev/disk/by-uuid/[DISK UUID]
command[check_cpuload]=/usr/local/nagios/libexec/check_load -w 15,10,5 -c 30,25,20
command[check_swap]=/usr/local/nagios/libexec/check_swap -w 10% -c 5%
command[check_raid]=/usr/local/nagios/libexec/check_raid
Monitor MySQL Service
MySQL Monitoring Requirements
- Monitor whether MySQL is running by checking port 3306.
- Monitor the availability of certain database '
testDB'.
MySQL Server Setting
When it comes to checking MySQL, it should be kept in mind that MySQL, by default, listens on only the loopback interface 127.0.0.1. This increases the security of the database. Manual tuning is needed to tell MySQL to listen on other interfaces as well. Here is how it can be done.
This setting is done on all MySQL servers.
root@nagios:~# vim /etc/mysql/my.cnf
The following line is commented out to make MySQL listens on all interfaces.
#bind-address = 127.0.0.1
Also, MySQL would not let just any host to connect to it. A user 'nagios' is created for both localhost and for 'any' host. This user is then granted all permission to all databases and will be used for monitoring.
The following settings are done for all MySQL servers.
root@nagios:~# mysql -u root –p
## MySQL root password here ##
A user 'nagios@localhost' is created in MySQL server.
mysql> CREATE USER 'nagios'@'localhost' IDENTIFIED BY 'nagios-pass';
mysql> GRANT ALL PRIVILEGES ON *.* TO 'nagios'@'localhost';
A user 'nagios@any-host' is created.
mysql> CREATE USER 'nagios'@'%' IDENTIFIED BY 'nagios-pass';
mysql> GRANT ALL PRIVILEGES ON *.* TO 'nagios'@'%';
mysql> FLUSH PRIVILEGES;
This should enable MySQL to listen on all interfaces, as well as accept incoming connections from user 'nagios' at any host.
Note that there are possible security implications of this change, so it's worth mentioning a few words:
- This setting will expose MySQL to all available interfaces, including WAN. It is vital to make sure only legitimate networks have access to the database. Filters such as firewall and TCP wrappers should be used.
- The MySQL '
nagios' user password should be very strong. If there are few Nagios servers, then MySQL user 'nagios@servername' should be created instead of 'nagios@%' i.e., any host.
Nagios Configuration for MySQL
The following tuning should do the trick.
define service{
use generic-service
host_name test-server-1
;hostgroup can be used instead as well
service_description Check MYSQL via TCP port
check_command check_tcp!3306
}
define service{
use generic-service
host_name test-server-1
;hostgroup can be used instead as well
service_description Check availability of database 'testDB'
check_command check_mysql_database!nagios!nagios-pass!testDB
;check_mysql!userName!userPassword!databaseName
}
This way, Nagios can help monitor the accessibility of both MySQL servers and the database stored within the servers.
Monitor Apache Web Server
Nagios can be used to monitor Apache web server as well.
Apache Monitoring Requirements
- Monitor whether the apache server is available.
This task is really easy as Nagios has a built-in command for this.
define service{
use generic-service
host_name test-server-1, test-server-2
service_description Check Apache Web Server
check_command check_http
}
Now that was really simple.
Monitor DNS Service
Nagios can monitor DNS service by asking the DNS server to either resolve a specific fully qualified domain name (FQDN), or by asking the server to use the dig tool. The default FQDN used for testing is www.google.com, but it can be changed as needed. The following file can be modified to do the job.
## The -H portion can be modified to replace Google ##
define command{
command_name check_dns
command_line /usr/lib/nagios/plugins/check_dns -H www.google.com -s '$HOSTADDRESS$'
}
Then edit the following file.
## Nagios asks server-3 to resolve the IP for google.com ##
define service{
use generic-service
host_name test-server-3
service_description Check DNS
check_command check_dns
}
## Nagios asks server-3 to dig google.com ##
define service{
use generic-service
host_name test-server-3
service_description Check DNS via dig
check_command check_dig!www.google.com
}
Monitor Mail Server
Nagios can monitor different mail server components like SMTP, POP, IMAP and mailq. As mentioned earlier, server-2 has postfix mail server set up on it. Nagios will be configured to monitor SMTP and mail queue of the server.
define service{
use generic-service
host_name test-server-2
service_description Check SMTP
check_command check_smtp
}
define service{
use generic-service
host_name test-server-2
service_description Check Mail Queue
check_command check_mailq_postfix!50!100
;warning at 50, critical at 100
}
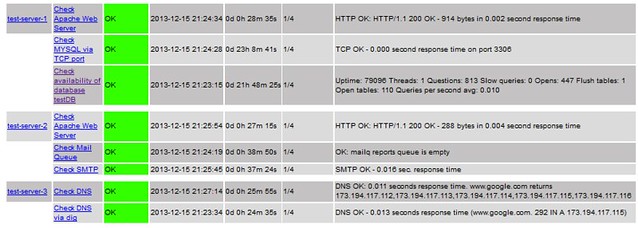
The following screenshot shows a complete overview of all the service checks that have been configured so far.
Port Based Monitoring for Custom Applications
Let us assume that the following custom application is also running in the network, listening on a particular port.
- Test Server 1: custom application (TCP Port 12345)
With a little tweaking, Nagios can help monitor this application port as well.
define service{
use generic-service
host_name test-server-1
service_description Check server 1 custom application
check_command check_tcp!12345
}
On a finishing note, Nagios can monitor many other sectors of a network. The scripts stored in /etc/nagios-plugins/config/ can shed some light on the awesome capabilities of Nagios.